Micro Business Quick Tips #1: Get a bullet proof E-Mail setup (SPF, DKIM, DMARC)
In the current world of spammers, intruders and fake emails, it is vital to get a bullet proof setup for your E-Mail deliveries. It took me some time to sort it out, but at the end not more than three steps are necessary to get an authenticated email setup with less spam risk and with better reputation, which reduces the risk that your emails are put into the spam folder by your client or prospects.
1. Get a own Domain with an associated Email Address
Using email addresses of a free mail provider isn’t a good idea when you start your business. Especially when you want to use third party providers for certain email based services over time. E.g. you could use
Mailchimp to send out a Email Newsletter on behalf of you.
The reason why you want your own domain based (and controlled) email address is that you want to decouple you from any DMARC policy decisions of the free email provider on its email domain.
DMARC is a global initiative (you will see later how you can benefit from it, a primer can be found
here) to reduce or stop fraudulent emails. All the big free email provider are participating and they may decide to strengthen the DMARC authentication policy. This will result in rejecting emails that claim to come for example from yahoo.com but actually originate at a non-Yahoo server.
This is a pattern definitely used by spammers, but for example also by Mailchimp when it will send out emails on behalf of your company (read the full story
here). Therefore get your own domain with its email address ([email protected]) in order to keep it under your control how you want to handle Emails sent on behalf of you by a untrusted or unknown source.
2. Setup Email Authentication in your DNS records
In order to ensure effective email delivery it’s highly recommended that you setup email authentication in your DNS records. By having purchased a own domain you also will get the possibility to adjust your DNS records (again you are in control). Depending where your purchased a domain the way how you update the records may vary. Search for DNS on the support page of your domain provider.
Email Authentication requires not only modification of the client side (by you adding DNS records) as well as Email provider which supports the
SPF and
DKIM on the server side. This is either the Email service provided with your domain or you go for one with the necessary support (you then have to modify the MX records of your DNS records to point to this new Email provider). Check the support pages of your domain email provider for keywords like SPF, DKIM to get an understanding what is supported.
For example I purchased a
Google Apps for Work account which comes with a very strong Gmail based E-Mail service offering. It can host all my different Email Addresses of all my different domains (around 10) and allows the setup of SPF/DKIM Email Authentication. The offering is overall very powerful (it introduces any kind of email relaying, rerouting etc. in case you run some other email account as well) and allows you to centralize all your Email handling.
In my DNS record of of my
cloudburo.net domain - which was purchased by another vendor - I had to reroute the mail traffic to the google email host environment (in DNS these are MX records). As you can see this a set of servers which will handle the traffic.
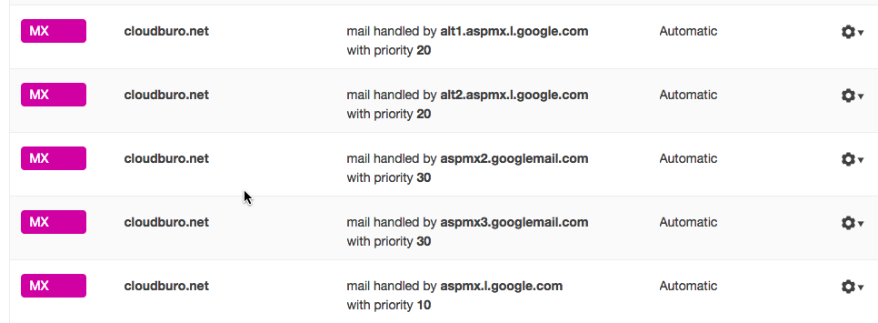
To get SPF and DKIM on your side established you have to create DNS records for
Sender-ID and
DKIM on your own domain.
Major ISP’s will use this DNS entries to verify your identity and track reputation. So it will ensure that your Emails will not land in the spam folder of your customers.
An example here the SPF DNS record entry which is used for my domain cloudburo.net. It defines that emails sent from
<name>@cloudburo.net may be coming from servers of
google.com (as explained above I host my emails with
google), as well as from
mtasv.net (this are the servers of Mailchimp which I use for newsletter distribution).

3. Start Monitoring your Email Traffic via a DMARC report
Having SPF and DKIM established you now can benefit from DMARC reporting to check unauthenticated usage of your domain email. You could even introduce a reject policy that is something I didn’t investigated it (definitely the large ISPs are starting to change their strategy as explained later)
DMARC stands for Domain-based Message Authentication, Reporting and Conformance. What DMARC does is allow domain owners to publish policy statements in DNS telling receiver domains what to do with messages that do not authenticate. In addition, DMARC introduces the concept of “domain alignment.” What this means is that the authentication has to be from the same domain (or a sub-domain) as the address in the header-from: line. The idea behind DMARC is that organizational owners can use SPF and DKIM authentication to authenticate their actual domain in the header-from line. This moves authentication from a important but behind the scenes technology out to an end user visible technology.
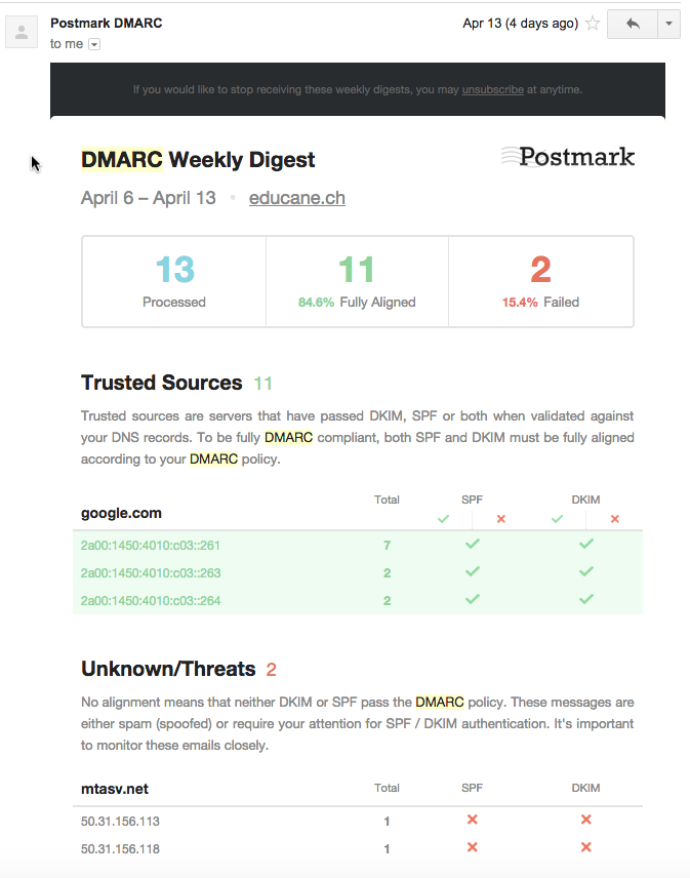
An excellent free reporting is provided by Postmark (
https://dmarc.postmarkapp.com/). By registering with them and again adding an additional DNS record for your domain, you will be delivered with a weekly DMARC report. Postmark will process reports from major ISPs about your domain’s DMARC alignment and turn the into beautiful, human-readable weekly email digests.
An example report is shown below, it shows two untrusted sources. A short lookup revealed that the IP addresses from mtasv.net belong to a third party provider which is used by me to send out Emails on behalf of me (actually it’s the very useful Postmark Transaction Email service which is integrated into applications of me). By checking their Web page I found the instruction how I could align these IP address with the DMARC policy (as you could think of by extending the DNS record).
You should now be well set up of with your Micro-Business to handle Email traffic in a spam-free manner and a high confidence that the email is reaching your end-user and not his spam folder.
Read the following
article by Yahoo which explains why the changed from one day to another to the hard DMARC policy. A journey to a spam free world.
In Friday afternoon last week, Yahoo made a simple change to its DMARC policy from “report” to “reject”. In other words, we requested that all other mail services reject emails claiming to come from a Yahoo user, but not signed by Yahoo. Y
ahoo is the first major email provider in the world to adopt this aggressive level of DMARC policy on behalf of our users.
And overnight, the bad guys who have used email spoofing to forge emails and launch phishing attempts pretending to come from a Yahoo Mail account were nearly stopped in their tracks.
comments powered by Disqus